Network, Server & Security

Security Solutions
Security is a Standard Not a Policy
Some bullet points highlighting the key aspects of Network, Firewall, and VPN :
Network:
– Facilitates communication and data transfer between devices.
– Enables connectivity and resource sharing within an organization.
– Supports efficient collaboration and productivity.
Firewall:
– Acts as a barrier between internal and external networks, controlling incoming and outgoing network traffic.
– Protects against unauthorized access, malware, and other network threats.
– Monitors and filters network traffic based on predetermined security rules.
VPN (Virtual Private Network):
– Provides secure remote access to internal network resources over the internet.
– Encrypts network traffic, ensuring confidentiality and data privacy.
– Enables remote workers to connect to the organization’s network securely, regardless of their physical location.
These points highlight the importance and benefits of network infrastructure, firewall implementation, and VPN usage in maintaining a secure and efficient network environment.

Know Cyber Security
Blue Chip collaborates with various verticals in Information Technology Services, offering expertise in the following areas:
Computer networking solutions involve the design, implementation, and management of computer networks to facilitate communication and data transfer between devices. These solutions can range from small-scale local networks within homes or offices to large-scale enterprise networks connecting multiple locations.
Here are some common components and considerations in computer networking solutions:
1. Network Architecture: This involves designing the structure and layout of the network, including the choice of network topology (e.g., star, bus, ring) and the selection of networking equipment (e.g., routers, switches).
2. Network Protocols: Protocols define the rules and procedures for data exchange between devices on a network. Common protocols include TCP/IP (Transmission Control Protocol/Internet Protocol) for internet communication, Ethernet for wired connections, and Wi-Fi for wireless connections.
3. Network Hardware: This includes networking devices such as routers, switches, modems, wireless access points, network interface cards (NICs), and cables. The selection of hardware depends on factors like network size, bandwidth requirements, and connectivity needs.
4. Network Security: Ensuring network security is crucial to protect sensitive data and prevent unauthorized access. This involves implementing firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), access controls, and encryption mechanisms.
5. Network Management: Network management involves tasks like network monitoring, performance optimization, configuration management, and troubleshooting. Various network management tools and software are available to streamline these activities and ensure the network operates efficiently.
6. Cloud Networking: Cloud-based networking solutions leverage cloud computing infrastructure to deliver network services. This includes virtual private clouds (VPCs), cloud-based routers and switches, and network-as-a-service (NaaS) offerings. Cloud networking offers scalability, flexibility, and cost-effectiveness.
7. Virtualization: Network virtualization technologies enable the creation of multiple virtual networks on a single physical network infrastructure. Virtualization provides enhanced network flexibility, simplified management, and efficient resource utilization.
8. Network Storage: Network-attached storage (NAS) and storage area networks (SANs) are used to provide centralized storage solutions accessible over the network. These solutions enable efficient data sharing, backup, and disaster recovery.
When seeking computer networking solutions, organizations often engage with network service providers or IT consulting firms that specialize in designing, implementing, and managing networks tailored to their specific requirements.
Please let me know if there is any specific aspect of computer networking solutions you would like to explore in more detail.
Firewall and Secure VPN Server Solutions
Firewall and secure VPN server solutions are essential components of network security that protect against unauthorized access and ensure secure communication between remote users and the corporate network.
Blue Chip specializes in providing robust firewall and secure VPN server solutions to enhance the security of your network and ensure secure remote access for your organization
A firewall is a hardware or software-based network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the Internet, to prevent unauthorized access and protect against cyber attacks.
A secure VPN (Virtual Private Network) server provides secure access to a private network over the public internet, enabling remote workers to securely access company resources as if they were directly connected to the internal network. VPNs use encryption and tunneling protocols to ensure the privacy and integrity of network communication and protect against eavesdropping, tampering, and other security threats.
Organizations can deploy firewall and secure VPN server solutions in-house or through cloud-based services offered by third-party vendors. It’s important to ensure that these solutions are configured and managed according to industry best practices and regulatory requirements to provide maximum protection against security threats.
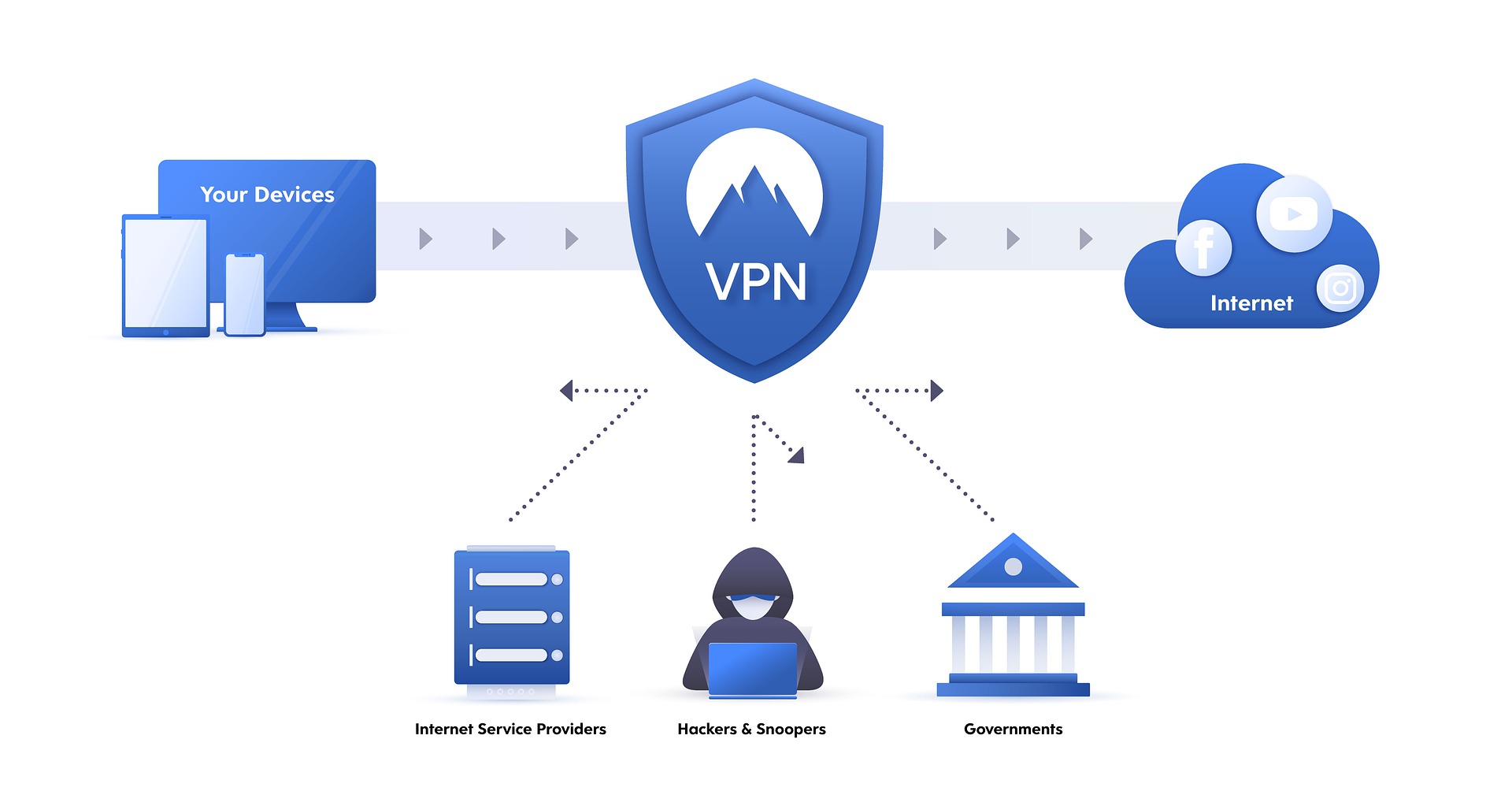
A secure network infrastructure with VPN and robust security measures is crucial for any organization to ensure data privacy, prevent cyber threats and unauthorized access, and maintain business continuity. Such solutions enable efficient data transfer and secure remote access for employees, while protecting sensitive information. Prioritizing network, VPN, and security solutions can help organizations build trust with customers and partners and ensure smooth operations.

